SMS is the most common way to verify users online. Sending one-time passwords (OTPs) via text makes signups more secure and prevents fake accounts. But attackers have learned how to turn this very mechanism against businesses. The result is a costly fraud known as SMS pumping.
What is SMS Pumping?
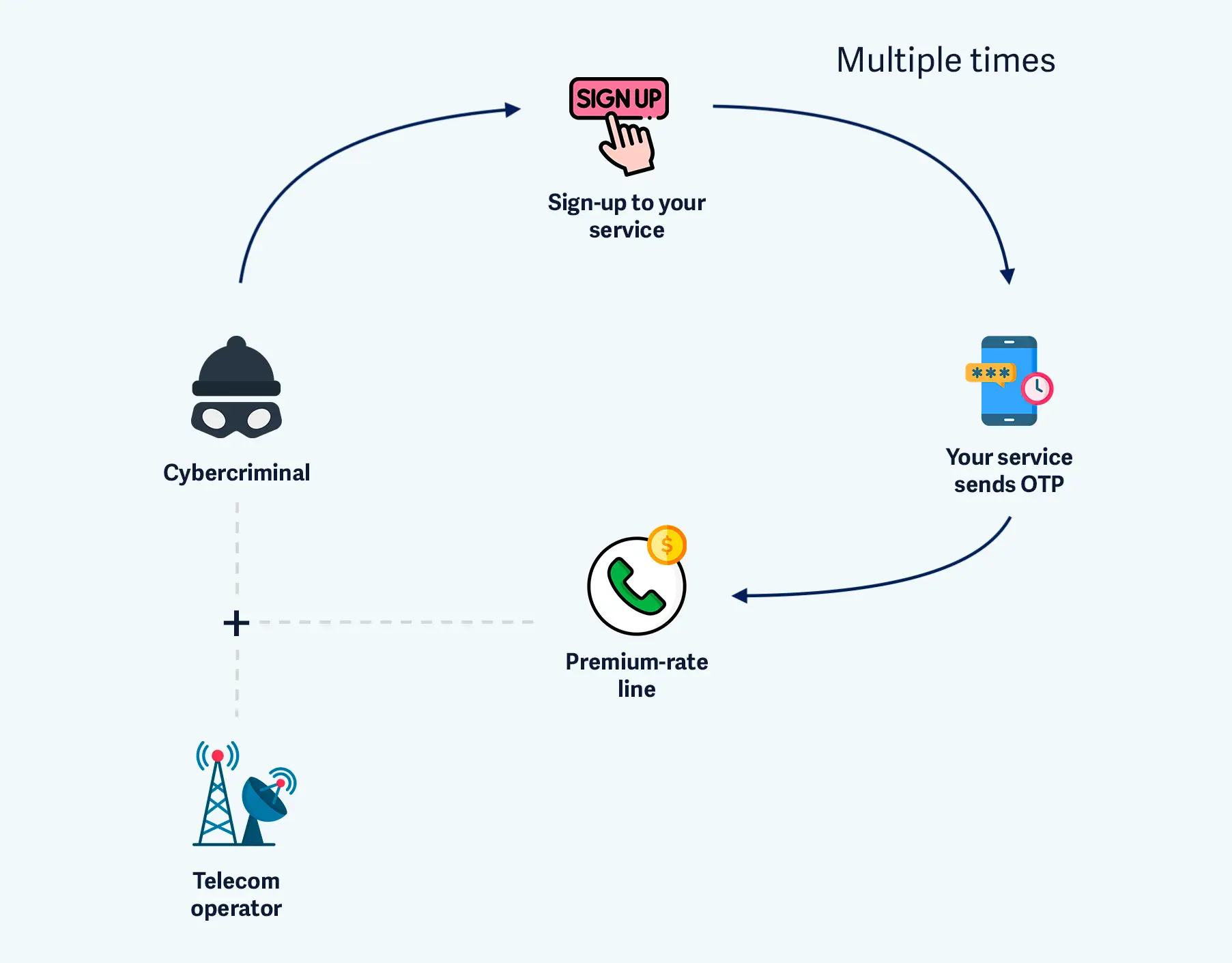
SMS pumping is a fraud technique where cybercriminals exploit your phone number verification or two-factor authentication (2FA) system for profit. Instead of paying you, they make you pay for messages sent to premium-rate numbers they control.
Here’s how it works:
- An attacker sets up premium-rate numbers with a telecom operator (these lines generate revenue when messages are sent to them).
- They deploy bots to create thousands of fake accounts on your app or website.
- Each fake account requests an OTP, forcing your system to send an SMS to the premium number.
- You pay your SMS provider for every message, while the attacker and telecom split the revenue.
By the time the fraud is spotted, thousands—or even millions—of SMS may have been sent, leaving your business with a shocking bill.
Real-World Case: Twitter’s $60M Problem
This type of fraud hit headlines in 2023 when Elon Musk revealed that SMS pumping was costing Twitter (now X) about $60 million per year in fake 2FA messages.
Twitter is getting scammed by phone companies for $60M/year of fake 2FA SMS messages
— Elon Musk (@elonmusk) February 18, 2023
In response, Twitter disabled SMS-based 2FA for non-paying users, a drastic step that shows how severe the financial impact of SMS pumping can be.
It’s Not Just SMS: Voice Calls Too
Some platforms offer automated phone calls instead of SMS—for example, to help visually impaired users. Unfortunately, the same trick applies.
Attackers register premium-rate phone lines that charge per minute. When your system calls these numbers to deliver codes, the attacker profits.
The Cost of SMS Pumping
The financial impact depends on your user base and messaging volume, but the risks are real:
- Direct costs: bloated SMS bills, sometimes running into tens of thousands of dollars before detection.
- Operational disruption: engineers pulled away from product work to fight fraud.
- Reputation damage: if fraud forces you to cut off SMS 2FA, user trust can suffer.
How to Detect an SMS Pumping Attack
Early detection is critical. Watch for these red flags:
- A sudden spike in OTP requests from new accounts.
- Large numbers of phone numbers that never complete verification.
- Requests coming from suspicious IP ranges or automated traffic patterns.
- Unusual concentration of OTP requests to specific country codes or prefixes.
SMS Pumping Protection: Best Practices
You don’t need to remove SMS 2FA like Twitter did. Instead, you can use layered defenses. Here are the most effective SMS pumping prevention strategies:
1. Screen phone numbers before sending OTPs
Use a phone number validation API to check whether a number is disposable, premium-rate, or high-risk. This lets you block fraudsters before they trigger costly messages.
If you're new to this, learn more about phone number validation API and how to detect fake ones.
2. Monitor traffic in real time
Look for spikes in OTP requests, repeated failures, and suspicious geographic clusters. Set alerts for anomalies so your team can act fast.
3. Rate limit OTP requests
Cap how many OTPs can be sent per user, per IP, or per device in a given window. This slows down bots and keeps costs under control.
4. Add secondary checks
When risk is moderate (e.g., a VoIP number), step up with an extra verification like email confirmation or CAPTCHA instead of sending an SMS right away.
5. Work with your SMS provider
Some providers offer fraud detection tools or can block messages to certain country codes and ranges known for abuse.
How NumCheckr Stops SMS Pumping
At NumCheckr, we focus on stopping fraud at the source: the phone number.
- Premium-rate detection: our algorithms and carrier data let us identify whether a number will generate premium charges.
- Disposable & virtual number detection: we track hundreds of thousands of fake, burner, and virtual numbers in real time.
- Fast & global: our API validates numbers in under 80 ms, with coverage in 120+ countries.
- Flexible: get instant checks in your signup flow, or bulk-validate entire user databases with CSV/Excel uploads.
By plugging NumCheckr into your registration process, every phone number is checked before an OTP is sent. If the number is premium-rate or disposable, you can block it or apply stricter checks.
This means fewer fake accounts, no surprise SMS bills, and a safer experience for your real users.
Final Thoughts
SMS pumping is a fast-growing fraud that turns your security feature into a liability. But with the right SMS pumping protection tools and layered defenses, you can stop it before it drains your budget.
Don’t wait until you see an unexpected bill. Implement SMS pumping prevention today with NumCheckr’s phone number validation API and protect your platform from this costly scam.
